When using SSO your users along with the login credentials are all managed outside of Kaizen
Kaizen can integrate with a customer’s SAML 2.0 single sign on. In this case users will authenticate through the customer’s identity provider (IdP) and not directly through Kaizen.
When a user successfully authenticates through the IdP they are passed through to Kaizen along with specific attributes about that user. The attributes that Kaizen needs at a minimum are First Name, Last Name, Email Address and a Unique Identifier. When a user which does not currently exist within Kaizen authenticates through the IdP Kaizen takes these attributes and uses them to create a new Kaizen account for that user. It is up to the customer and the IdP to control which users should have access to Kaizen and which should not.
When a user is authenticated the IdP specifies the lifetime (max time) for which the session between the user’s browser and Kaizen should be valid. Once this time period expires the user’s session will no longer be valid and the user will be logged out. Kaizen sets a default value for 8 hours, if the value coming from the IdP is less than this then this is used instead.
Alongside the session lifetime there is also session inactivity. The IdP sets a session inactivity time value per application that the user is authenticated for. Every time a user is actively using Kaizen they are making periodic requests to the server. If no activity occurs within Kaizen for the duration of the time period set as the session inactivity then the user will be logged out by the IdP.
Configuring SSO
Our metadata can be found at:
For our UK and EU customers: https://kaizenep.com/sp/shibboleth
For our Australian customers: https://au.kaizenep.com/sp/shibboleth
For our Canadian customers: https://ca.kaizenep.com/sp/shibboleth
In order to complete the setup process we will need:
Your metadata
An agreement on which constant and unique attribute we can use to identify a user. Usually it is eduPersonPrincipalName (urn:oid:1.3.6.1.4.1.5923.1.1.1.6)
An email, usually urn:oid:0.9.2342.19200300.100.1.3
We can also use other attributes, for example givenName urn:oid:2.5.4.42 or surname urn:oid:2.5.4.4
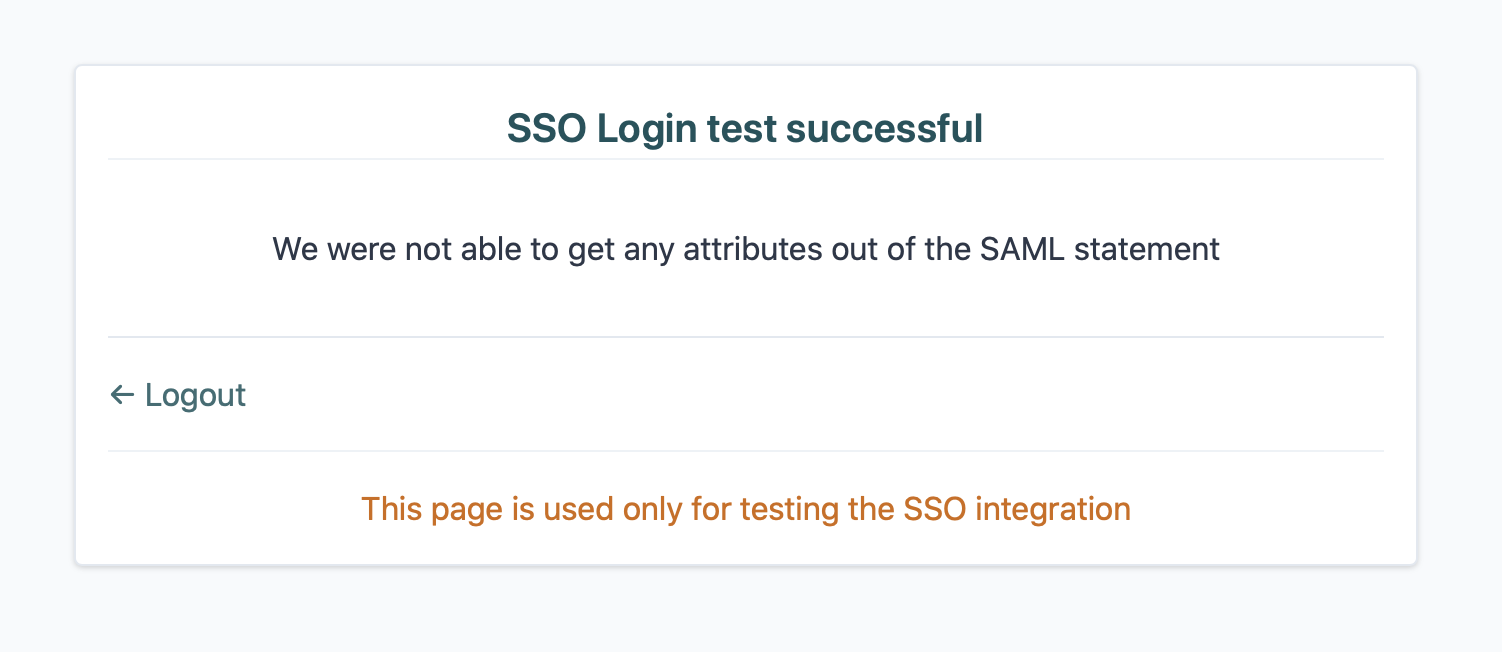
Once we have received the above information and setup this configuration we can perform test logins to ensure it's working as expecting. This is done away from the live instance through the following steps:
Accessing a link unique to your organisation (https://auth.[region].kaizenep.com/test/saml2/[org_ID])
Entering login credentials
Determining whether the resulting status page shows a successful test login and providing us with a screen shot. This will help us validate whether all the correct attributes are being passed through
Once we have validated the test login is successful we are ready to provide the SSO login link directly onto the live instance when it is appropriate to do so.